In today’s interconnected world, the security of your business hinges on the protection of its most vulnerable points; its endpoints. Whether it’s your employees’ laptops, mobile devices, desktops, or servers, these endpoints serve as entry points for cybercriminals to exploit. As businesses become more reliant on digital technologies, the need for robust endpoint protection has never been greater.Continue reading “Choosing the Best Endpoint Protection for Your Business: A Comprehensive Guide”
Category Archives: How-to
The Red Team vs. Blue Team in Cybersecurity: A Comprehensive Guide
The terms “Red Team” and “Blue Team” have become fundamental in understanding how organizations approach threat detection, defense, and overall security posture. Both teams have unique, complementary roles, working together to improve an organization’s ability to prevent, detect, and respond to cyber threats. Whether you’re an aspiring cybersecurity professional or an organization looking to enhanceContinue reading “The Red Team vs. Blue Team in Cybersecurity: A Comprehensive Guide”
About the day I found out my centOS 9 virtual machine didn’t have the “whatis” command enabled.
Today I started practicing some of the basics on a virtual machine I recently created on UTM. The linux distribution was CentOS 9 and I noticed the “whatis” command was not recognized for some odd reason. At some point I forgot the root password and I was unable to run the “mandb” command. So, hereContinue reading “About the day I found out my centOS 9 virtual machine didn’t have the “whatis” command enabled.”
An Ethical Guide to Assessing WPA2 and WPA3 Network Security
Wireless network security is critical to both personal and enterprise systems, given the increasing volume of sensitive data transmitted over Wi-Fi. As cybersecurity professionals, learning to assess WPA2 and WPA3 network security is essential for identifying potential weaknesses and strengthening defenses against unauthorized access. This guide introduces ethical techniques, tools, and best practices for penetrationContinue reading “An Ethical Guide to Assessing WPA2 and WPA3 Network Security”
Creating Local Domains for Cybersecurity Testing on Kali Linux
Cybersecurity practitioners and ethical hackers often need to simulate real-world environments to test security tools, configurations, and response protocols. Setting up a controlled environment with a local domain helps in testing techniques like phishing simulations, DNS-based attacks, and malware analysis—all while keeping tests secure and private. Here’s how to create a local domain in KaliContinue reading “Creating Local Domains for Cybersecurity Testing on Kali Linux”
Why Secure, Custom Modular Keyboards Matter in Cybersecurity
Keyboards with encrypted connections are crucial for protecting against interception attacks, especially in wireless setups. Here’s why building secure, custom modular keyboards is becoming increasingly essential: By building secure modular keyboards, cybersecurity professionals and enthusiasts can create customized, resilient devices that prevent common wireless attacks, support encrypted connections, and improve overall data protection in digitalContinue reading “Why Secure, Custom Modular Keyboards Matter in Cybersecurity”
Top 10 Cybersecurity Tools Every Beginner Should Know
In cybersecurity, building a toolkit of essential tools is the foundation for effective learning and skill-building. Whether you’re just starting or want to reinforce your basics, here’s a breakdown of the top 10 tools, why they’re useful, and how to start. 1. Wireshark 2. Nmap (Network Mapper) 3. Metasploit 4. John the Ripper 5. Burp Suite 6. Kali Linux 7. Snort 8. NiktoContinue reading “Top 10 Cybersecurity Tools Every Beginner Should Know”
How to develop soft skills?
In a world where technical skills and certifications are often seen as the gateway to success in tech roles, soft skills—those non-technical, interpersonal abilities—are increasingly recognized as equally crucial. Whether you’re a support engineer, data analyst, or developer, having a strong foundation in soft skills can elevate your career, making you not only a moreContinue reading “How to develop soft skills?”
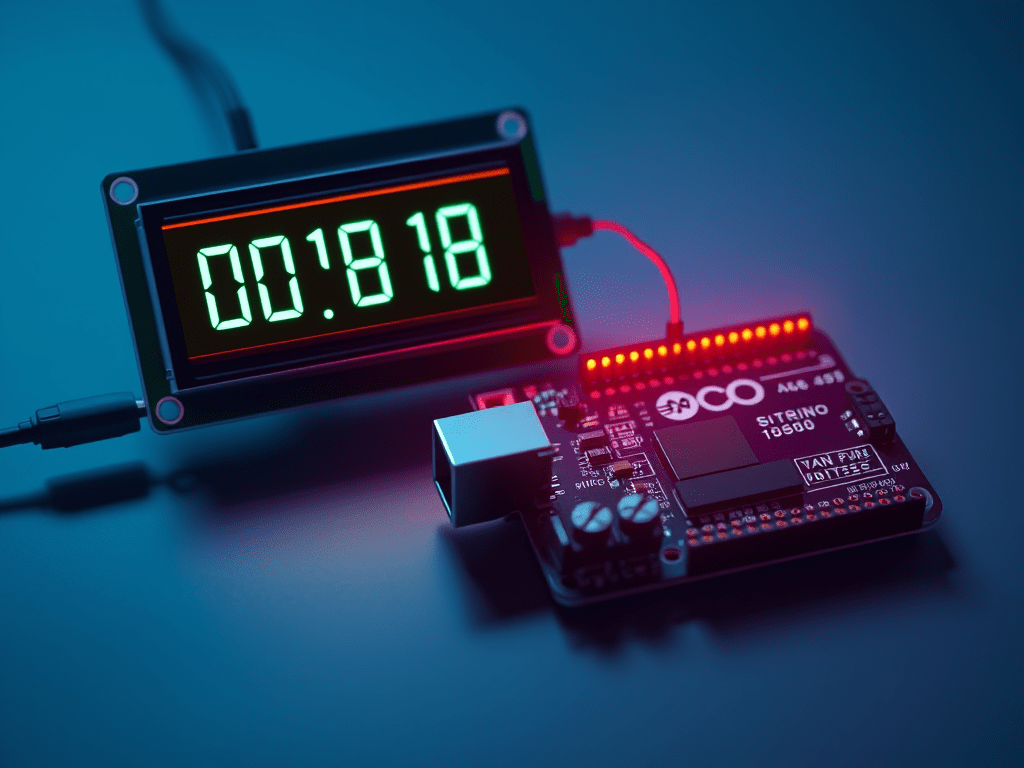
Binary to Decimal Converter using Arduino UNO.
This is quick excessive developed by myself with the following specific objectives: First, let’s start with the materials required. I used Tinkercad to build and program this project. Here is the electronics diagram. And here is how it looks like on the simulator. What it does is let the user input a 4 bit binaryContinue reading “Binary to Decimal Converter using Arduino UNO.”