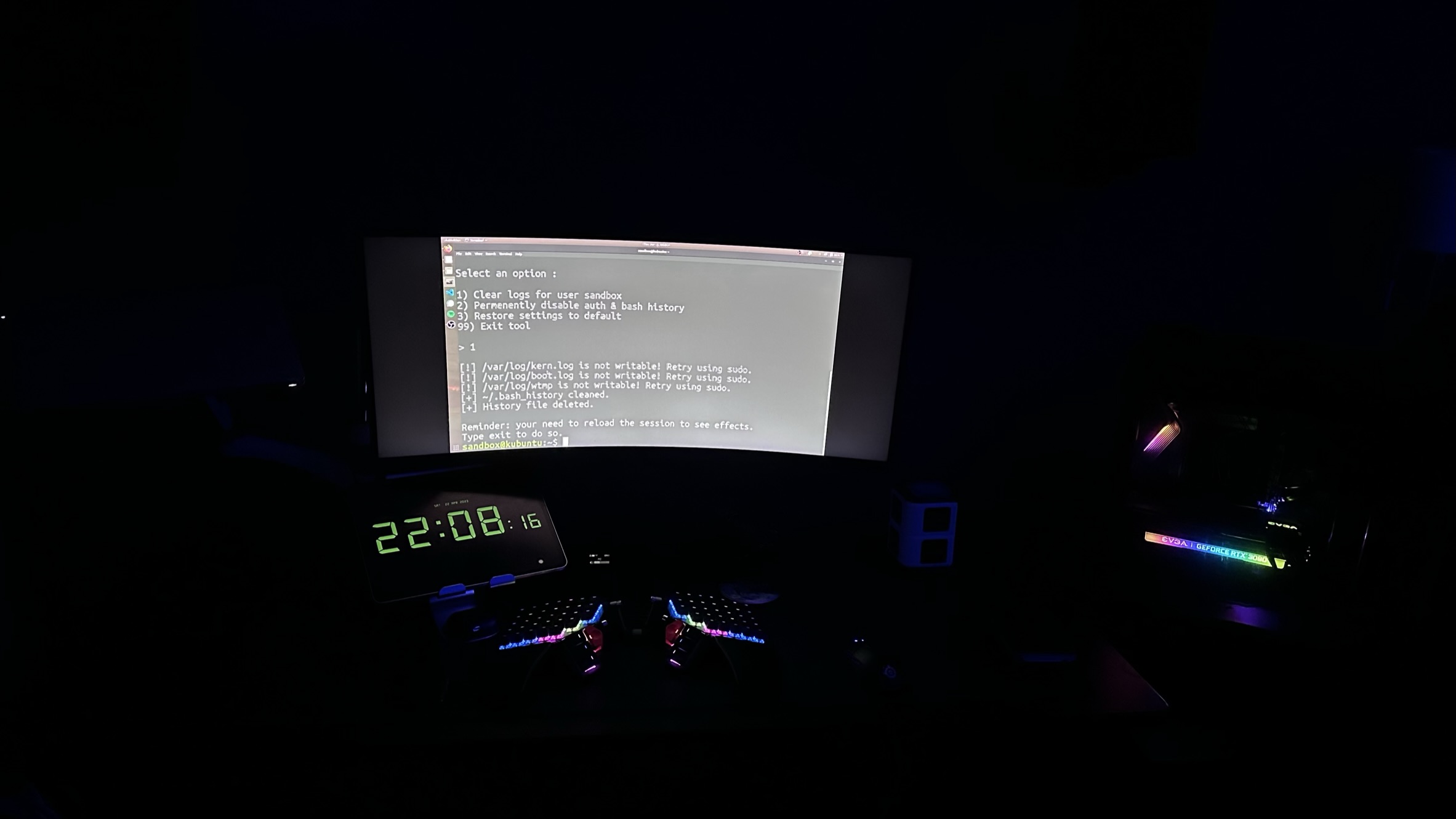
-yet another milestone leak
Welcome to project inet802.
A website designed for self-learning purposes.
- Choosing the Best Endpoint Protection for Your Business: A Comprehensive GuideIn today’s interconnected world, the security of your business hinges on the protection of its most vulnerable points; its endpoints. Whether it’s your employees’ laptops, mobile devices, desktops, or servers, these endpoints serve as entry points for cybercriminals to exploit. As businesses become more reliant on digital technologies, the need for robust endpoint protection has never been greater.Continue reading “Choosing the Best Endpoint Protection for Your Business: A Comprehensive Guide”
- The Red Team vs. Blue Team in Cybersecurity: A Comprehensive GuideThe terms “Red Team” and “Blue Team” have become fundamental in understanding how organizations approach threat detection, defense, and overall security posture. Both teams have unique, complementary roles, working together to improve an organization’s ability to prevent, detect, and respond to cyber threats. Whether you’re an aspiring cybersecurity professional or an organization looking to enhanceContinue reading “The Red Team vs. Blue Team in Cybersecurity: A Comprehensive Guide”
- Python in Cybersecurity: A Powerful Tool for Defense and Offensive OperationsIn the fast-evolving world of cybersecurity, Python has established itself as one of the most versatile and powerful programming languages for both defensive and offensive operations. With its simple syntax and rich ecosystem of libraries, Python has become a go-to tool for security professionals, penetration testers, malware analysts, and incident responders. In this article, weContinue reading “Python in Cybersecurity: A Powerful Tool for Defense and Offensive Operations”
- About the day I found out my centOS 9 virtual machine didn’t have the “whatis” command enabled.Today I started practicing some of the basics on a virtual machine I recently created on UTM. The linux distribution was CentOS 9 and I noticed the “whatis” command was not recognized for some odd reason. At some point I forgot the root password and I was unable to run the “mandb” command. So, hereContinue reading “About the day I found out my centOS 9 virtual machine didn’t have the “whatis” command enabled.”
- Kali Linux, Parrot OS, or BlackArch Linux?Selecting the right Linux distribution for penetration testing is crucial for professionals and enthusiasts in cybersecurity. With multiple options available, each with unique features and drawbacks, this guide will help you evaluate Kali Linux, Parrot OS, and BlackArch Linux for your needs. We’ll also address common installation issues on virtual hypervisors like VirtualBox and VMware. Overview of Each DistributionContinue reading “Kali Linux, Parrot OS, or BlackArch Linux?”